Cloud Security Posture Management (CSPM)
Gain continuous visibility across AWS, Azure, GCP, and hybrid environments. Get full context into applications, data, and AI models so you can instantly prioritize risks and remediate with confidence.
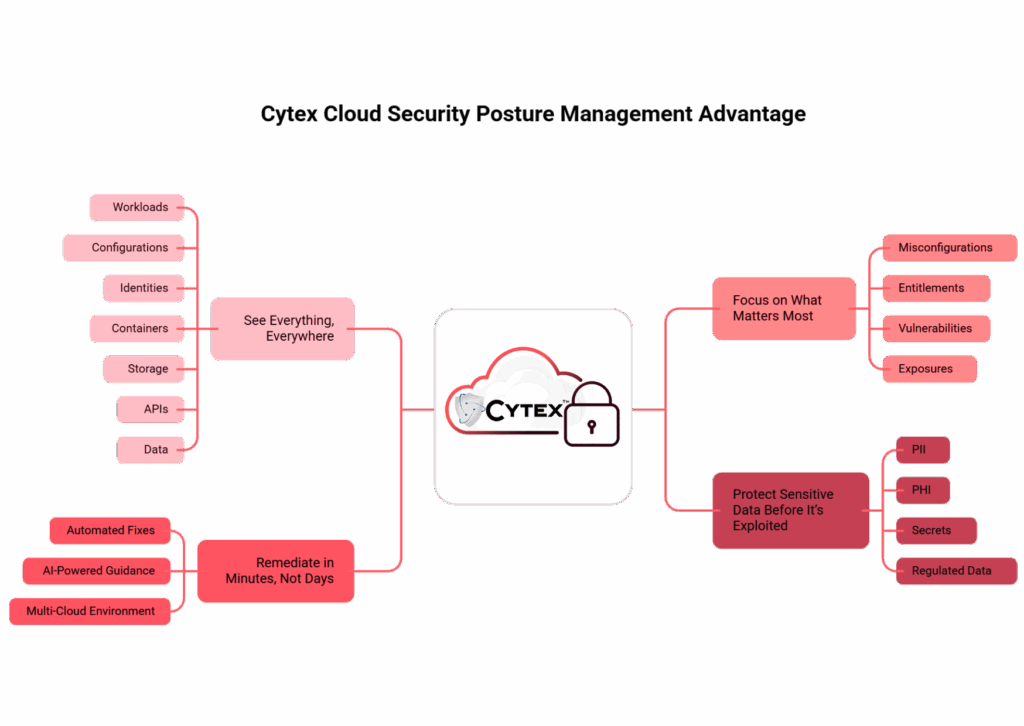
See Everything, Everywhere
Get real-time visibility across workloads, configurations, identities, containers, storage, APIs, and data in AWS, Azure, GCP, or on-premises, all from one intuitive dashboard.
Focus on What Matters Most
Stop chasing noise. Cytex connects misconfigurations, entitlements, vulnerabilities, and exposures into clear, scored attack paths reducing false positives and alert fatigue so you can act fast on critical risks.
Remediate in Minutes, Not Days
Automate routine fixes instantly and leverage AI-powered guidance for precise instructions and code. Slash mean time to remediation (MTTR) and ensure every fix works across your multi-cloud environment.
Protect Sensitive Data
Continuously scan every workload to uncover PII, PHI, secrets, and regulated data. Prioritize and block exploitation paths proactively to turn exploitation risks into non-events.
Cytex CSPM Advantage
Why settle for complexity?

Cytex CSPM Advantage
Turn Compliance Into Your Cloud Advantage
Traditional CSPM only checks configurations, leaving workloads exposed. Cytex goes further, delivering full-stack visibility and intelligent risk prioritization so you can focus on what matters most. Achieve faster remediation, stronger security, and continuous compliance without guesswork.

See Everything, Everywhere
Get real-time visibility across workloads, configurations, identities, containers, storage, APIs, and data in AWS, Azure, GCP, or on-premises, all from one intuitive dashboard.

Focus on What Matters Most
Stop chasing noise. Cytex connects misconfigurations, entitlements, vulnerabilities, and exposures into clear, scored attack paths reducing false positives and alert fatigue so you can act fast on critical risks.

Remediate in Minutes, Not Days
Automate routine fixes instantly and leverage AI-powered guidance for precise instructions and code. Slash mean time to remediation (MTTR) and ensure every fix works across your multi-cloud environment.

Protect Sensitive Data
Continuously scan every workload to uncover PII, PHI, secrets, and regulated data. Prioritize and block exploitation paths proactively to turn exploitation risks into non-events.
Unified Cloud Security & Compliance
Continuous Multi-Cloud Security & Compliance
Take control of your entire cloud ecosystem with Cytex. Get coverage across workloads, configurations, identities, containers, and data, while aligning policies seamlessly across AWS, Azure, GCP, and hybrid environments.
Advanced CSPM
Cloud App Security That Works as Hard as You Do
Secure your entire cloud footprint SaaS, AI applications, LLMs, and beyond with data discovery, continuous posture control, and streamlined compliance that automatically adapts to evolving regulations and best practices.
Find Sensitive Data Before Attackers Do
Cytex continuously identifies PII, PHI, secrets, and sensitive data, including AI models, training data and agentic workflows. With data classification and breach-cost impact analysis, you’ll know exactly what to protect and why.
Fix Issues Fast with AI
Close gaps before they become breaches. Cytex delivers prioritized action plans with recommended fixes based on best practices, plus role-based access control enforcement to maintain least privilege across assets.
Stay Audit-Ready Without the Hassle
Gain real-time visibility and risk profiling for every cloud app. Embedded compliance checks strengthen your security posture and keep you audit-ready without adding complexity or manual effort.
Advanced CSPM
Secure Productivity Apps.
Strengthen Your Security Posture.
Your productivity can also turn into your fastest-growing risk surface. Unapproved apps, excessive permissions, and sensitive data scattered across productivity tools and emerging AI platforms create risk blind spots that attackers, auditors, and regulators notice first.

Identify & Prevent Data Exfiltration Risks
Discover, classify, and protect PII, PHI, secrets, and sensitive data including AI models and training data to reduce the risk of data exfiltration.

Adopt Continuous Compliance
Continuous security controls across every app, eliminate surprise findings & last-minute fire drills. Centralized policy management continuously removes non-compliant settings and over-permissions.

Quantify Risk and Act Fast
Attach breach-cost analysis to every sensitive data finding so leadership instantly understands the impact and the urgency of taking action.

Reclaim Control & Build Trust
Reduce excessive permissions, eliminate shadow IT, and enforce least privilege with automated remediation plans & role-based access controls to strengthen security posture across the enterprise.
Forward-thinking security teams choose Cytex to make cloud protection continuous, compliant, and operationally efficient




